How to register an application in Microsoft Entra ID (formerly Azure AD) to enable Single Sign On that works with Impero
Note: Microsoft Entra ID is the new name for Azure Active directory (AD). All licensing and functionality remain the same. Find more information on the official website.
- Search for “Microsoft Entra ID”

- On the left side menu, click in “App Registrations”

- Click on the top menu item “New Registration”

- In the next page you’re presented with some fields. For “Name” and “Supported account types” choose what suits you.
For “Redirect URI”, despite the name, it’s important to choose the application type as “Single-page application (SPA)” and the URL it needs to respect the pattern: https://MY_ORG_NAME.impero.com/api/single-sign-on where “MY_ORG_NAME” is the name of your organization that you use to access Impero. If you don’t have one yet or don’t know which one it is, ask our customer support via https://support.impero.com/knowledge/kb-tickets/new

You can click on “Register” and the application will be created. - The next step is to send some information to Impero in order for us wire your configuration in our system. Go to the “Overview” page of the new recently application and copy the following information: “Application (client) ID” and “Directory (tenant) ID” (we don’t need “Object Id” or any kind of Client Secret) and send this information to your point of contact in Impero.

We’re going to answer as soon as possible in order to make sure you can test the integration.
At this point, if an Entra ID user from your organization also has an Impero account, it will be possible for them to log in to Impero using Single Sign On (SSO).
Troubleshooting
The default configuration and API permissions should be enough for the integration to work but in case you have problems you can check if:
1. Configured available tokens: go to “Authentication” on the left menu side and make sure the options for the field “Select the tokens you would like to be issued by the authorization endpoint:” are NOT selected (if Authorization flow is in use).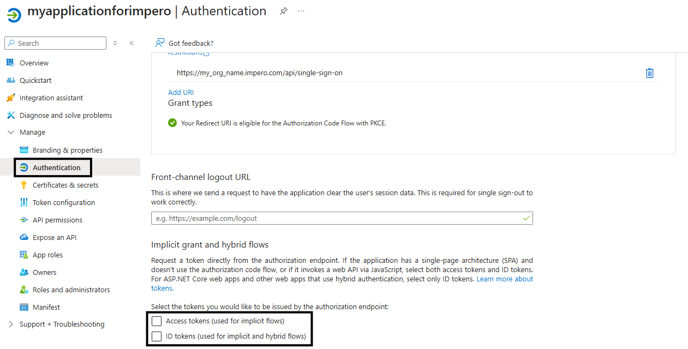
Cautious: In case you need to set up multi-factor authentication with exceptions, please use the implicit flow instead of authorization flow. Further, you need to enable ID tokens by ticking the box for "ID tokens (used for implicit and hybrid flows)" as above.
2. API permissions: go to “API permissions” on the left menu side and make sure to enable the permissions like the image below

In case of any questions, please don’t hesitate to contact us at support@impero.com